CYBER SECURITY /PENETRATION TEST | DATA PROTECTION INFORMATION SECURITY | CERTIFICATION
simple, flexible and affordable.
Dear visitor,
i am glad that you are visiting our website.
we are a leading one-stop service provider for cyber security, penetration testing, data protection(privacy), information security and company certification.
Our certified consultants, penetration testers and IT specialists have many years of experience.
Based on national and international experience in the areas of diplomatic corps (embassies, foreign office), critical infrastructure (water supply, sewage plants, train services), public administration (courts, town halls) and private sector (Apple, Siemens, O2 Telefonica Germany, PAYBACK Germany, Saudi Telecom) we are able to provide industry-specific and unique cyber security (99%).
We offer multilingual services (English, German) globally.
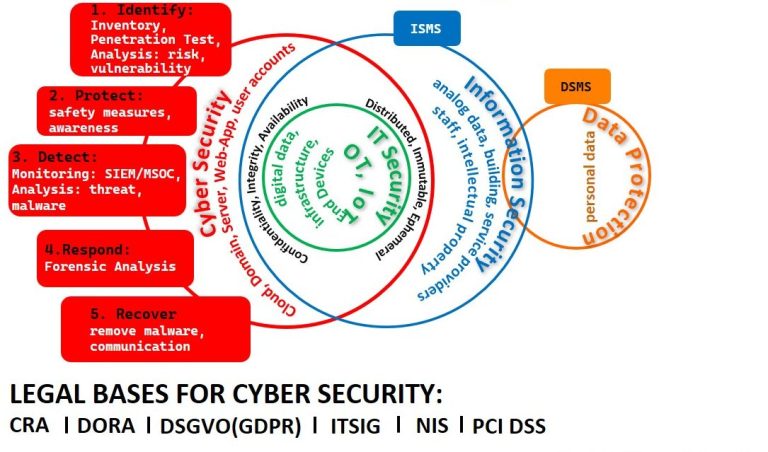
We believe that comprehensive, proactive and seemless cyber security is neither optional nor a luxury. It is an existential necessity which is also legally required (see image above "legal bases for system security")
Comprehensive security consists of four components:
- Cyber security (penetration testing, cyber liability insurance, data protection and information security)
- Awareness training for employees
- Monitoring of IT systems
- Structure security (inventory insurance, alarm, video surveillance and privacy shield)
Data controller needs to make sure that IT systems fulfil the legal requirments and they operate at the defined performance level in accordance with Sevice Level Agreements (SLA).
Unauthorized data access needs to be prevented and cyber attacks need to be thwarted.
Anomalies have to be proactively detected prior to detection by customers, citizens, authorities, investors or attorneys of competitors.
Tangible damages (penalties, costs for IT system recovery) and intangible damages (reputation) need to be avoided and mitigated.
Cost calculation and probability of occurance for future cyber damages isn't easy because it depends on individual perception of risk.
Extrapolation of previous cyber damages (e.g. by phishing attacks) can be useful for the calculation of Return On Security Investment (ROSI).
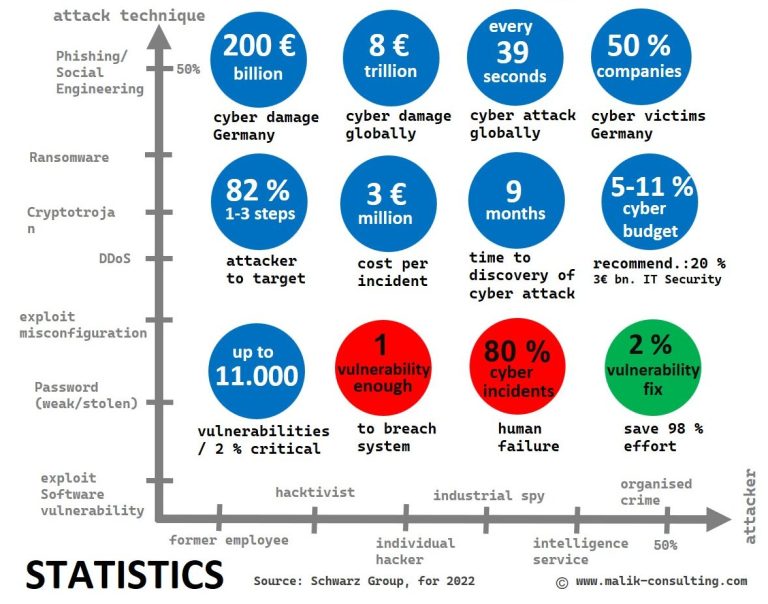
By fixing 2% of the relevant vulnerabilities you can reduce 98% of effort for system hardening.
Professional hackers require just a single (critical) vulnerability to breach your IT systems (see image above “Statistics”).
Penetration tests need to be repeated as the hackers adapt their methods to technological advancements and can easily circumvent the usual safety measures (firewall, antivirus program).
During penetration tests, we don't just rely on signature-based (known threats) recognition but also use heuristic methods to identify new threats.
In order to successfully repel cyber attacks, not only strong IT skills, experience and passion are required but also knowledge of geopolitics and human nature is needed because some hackers (intelligence services and hacktivists) have political motives.
80% of cyber incidents and data breaches can be traced back to human failure. This proves that the compliance based awareness trainings do not deliver the desired results (see image above “Statistics”).
Holistic awareness approach helps creating a security culture and positively influence employee behaviour.
The "right to be forgotten" (GDPR) can't always be implemented because the users often have an irreversible digital footprint on the internet and don't even realize that their personal data is being sold on the Dark Web.
I am looking forward to present our comprehensive security approach in a personal meeting.


© Urheberrecht. Alle Rechte vorbehalten.